I will be looking at this very closely, as it sounds like it might fit a specific need I have (and with a soft deadline only a week away) very well.
I had been looking at the Encrypt Tiddler Plugin - which encrypts whole tids, and has the downside of being fully decrypted (and via node, saved to disk) as soon as it’s decrypted in browser, and then requiring encryption all over again (to then save the crypt version to disk)
A secret that isn’t the whole tid, and which is ALWAYS kept encrypted (and only unencrypted in-browser) is kind of perfect.
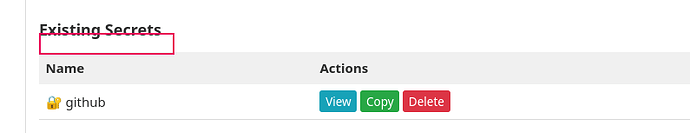
At first glance my thoughts are not from a security perspective (I simply dont have the skills beyond very basics), but from a UI perspective - I think the Vault Manager should have ‘view’ and ‘copy’ columns. Maybe ‘duplicate’ and ‘edit’ functions too? - I see the vault has metadata about each secret, which looks to be prepared for the possibility of editing secrets. That created and modified metadata should be visible in the vault too. I’d also suggest within the metadata, a non-encrypted comment to go with each secret
Within rendered content. I think it’d help to have the ‘copy’ button in the non-revealed form - maybe use the typical ‘copy’ icon ($:/core/images/copy-clipboard)? The revealed secret being between the title and the copy icon would then
When adding a secret, it’d be good to be able to view what’s being added. At the moment if I add a secret, it’s typed hidden, and to check I have it right, I have to save the secret, then add it to a tid!
Oh, and testing that I just found the order of secrets within the editor menu item, is confusingly different to the order within the vault (toolbar seems to be in alphabetical order, vault seems to be in added order).
Anyway, I didn’t mean to write so much straight up! I’m coming from a place of enthusiasm here! 


 .
. ). In the future when this plugin matures, perhaps it could add a few custom importers/exporters for a GPG-compatible vault encrypted dump, a KeePass (which has a CLI-only mode) database or a
). In the future when this plugin matures, perhaps it could add a few custom importers/exporters for a GPG-compatible vault encrypted dump, a KeePass (which has a CLI-only mode) database or a