Attempting to unlock a vault from the vault manager reveals this in-page error:
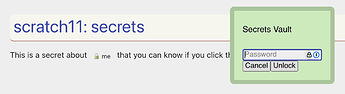
However, if you click a secret when the vault is locked, you get the green vault prompt:
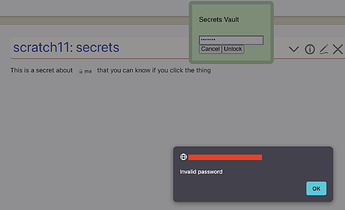
and failing the password there, returns an alert popup
That alert popup is what bothers me - I think all UI elements should be within TW
Also, a failure by this mode doesn’t inform of the lockout attempts remaining.
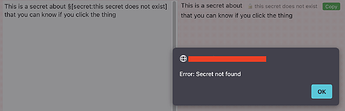
The other place that generates this alert popup is when you click a secret that doesn’t exist (I edited this one to mock it up, but originally encountered it by deleting a secret after adding the wikitext code for it)
Another thing I just noticed in testing:
Having a colon in the title messes things up.
From a fresh vault (which is a .tid in my node setup), I add this secret:
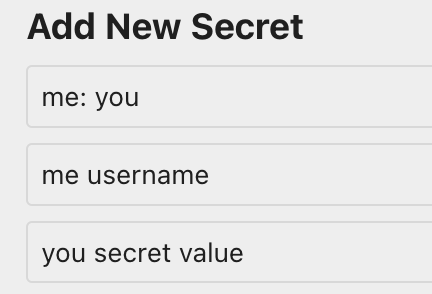
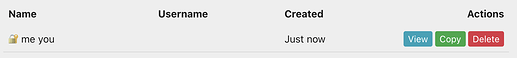
However the name has lost the colon, and the username isn’t shown at all:
Looking behind the scenes, the vault is now converted to a json, with the colon dropped from the secret- and meta- field names, but not the username- field name. IMHO any characters should be valid for the name, though I recognise this will complicate things, or give info and about valid/invalid characters within the name before saving. (Looks like []{}() are all similarly removed, I’ve not tested weird characters in the title beyond these seven)
This also has me noticing that the username is not encrypted, which I feel like it should be.
I should note - for my own intended use, this is already great - I currently don’t see my needs for the secrets stored in TW to require more than this already does. But thinking on the systems I’ve used (personal and professional, ranging from commercial products to home-grown wrapper scripts around gpg), I think my minimum requirements of what I’d want for a general purpose secret stash are:
- Four fields: name, username, secret, comment.
- Name and Username both single line, secret and comment multiline (storing SSL certs and keys is common in work secret stores for instance).
- Name and Comment public, username and secret encrypted
- Name and Secret as required fields, username and comment as optional
- …I’m sure I had a second thing to note, but between investigating the
:[]{}() thing, and then lunch it’s entirely escaped my mind and eluded any attempts to think of it again!